New Projects Involving Hardware and Network Programming
Sat, 14 Nov 2009 4:08:07 EST
Since I graduated from college, my independent work has been focused on learning techniques for unique distance communication. I knew long before I graduated college that in order to work at a fun job, I would have to move away from my family. My family lives in the middle of nowhere in a rural farming community in Michigan. They currently utilize EV-DO for an Internet connection which proves to be sporadic because they are on the edge of the coverage map. This hardware and software is directly targeted at their situation.
I have decided that my next major learning endeavor is to further my education in network programming. Last year at work I got to do some socket communication programming between Flash and a C# application that allows several mice to be used at once. This is implemented in the Hershey Story Explore Hershey map table. It allows four mice to be uniquely used at once with a single Flash application.
I am excited to learn how peer-to-peer applications punch holes through firewalls in order to allow communication between two clients without bogging down a central server. In the papers I have read thus far, it looks like there is no central way to do this. The trick seems to be that you have to try several different methods of communication until you find one that works. Even more cool is that in using these techniques you have to authenticate your connections because they might mistakenly connect to incorrect hosts. You also have to obfuscate your traffic because apparently certain firewalls/routers will inspect packets leaving them and alter the contents if they include plain text IP addresses and ports.
I have found two excellent papers outlining the methods involved in NAT traversal techniques. For a great overview the paper "NAT Traversal Techniques and Peer-to-Peer Applications" by Zhou Hu is a great read. It seems like the most widely successfully technique is UDP/TCP hole punching, so the second paper, focused on that topic is: "Peer-toPeer Communication Across Network Address Translators" by Bryan Ford, Pyda Srisuresh, and Dan Kegel.
I am planning to use Java in order to implement these techniques, so another great practical resource has been the source code of the popular bittorrent application Azureus/Vuze. By looking through that I have learned about NATPMP, and the unrelated but cool concept of MagnetURI so far.
In deciding what sensors to use, I came across a fun paper called "Squeeze Me: A Portable Biofeedback Device for Children" by Amy Parness, Ed Guttman, and Christine Brumback. They created a device from Dragon Skin Silicone that children can use to assist in rehabilitation from injury. I settled on pressure based resistors. Time will tell how well they work out.
About the Network Programming
During the development of my flash controlled RC car and custom hardware for it, (the RC Interceptor) over the past year I have been sitting on several ideas that I wanted to work on. Now that I am just waiting for Crunchbang Linux to release their version of Ubuntu 9.10 to demonstrate the car, I have been able to move on to other exciting projects.I have decided that my next major learning endeavor is to further my education in network programming. Last year at work I got to do some socket communication programming between Flash and a C# application that allows several mice to be used at once. This is implemented in the Hershey Story Explore Hershey map table. It allows four mice to be uniquely used at once with a single Flash application.
I am excited to learn how peer-to-peer applications punch holes through firewalls in order to allow communication between two clients without bogging down a central server. In the papers I have read thus far, it looks like there is no central way to do this. The trick seems to be that you have to try several different methods of communication until you find one that works. Even more cool is that in using these techniques you have to authenticate your connections because they might mistakenly connect to incorrect hosts. You also have to obfuscate your traffic because apparently certain firewalls/routers will inspect packets leaving them and alter the contents if they include plain text IP addresses and ports.
I have found two excellent papers outlining the methods involved in NAT traversal techniques. For a great overview the paper "NAT Traversal Techniques and Peer-to-Peer Applications" by Zhou Hu is a great read. It seems like the most widely successfully technique is UDP/TCP hole punching, so the second paper, focused on that topic is: "Peer-toPeer Communication Across Network Address Translators" by Bryan Ford, Pyda Srisuresh, and Dan Kegel.
I am planning to use Java in order to implement these techniques, so another great practical resource has been the source code of the popular bittorrent application Azureus/Vuze. By looking through that I have learned about NATPMP, and the unrelated but cool concept of MagnetURI so far.
About the New Hardware
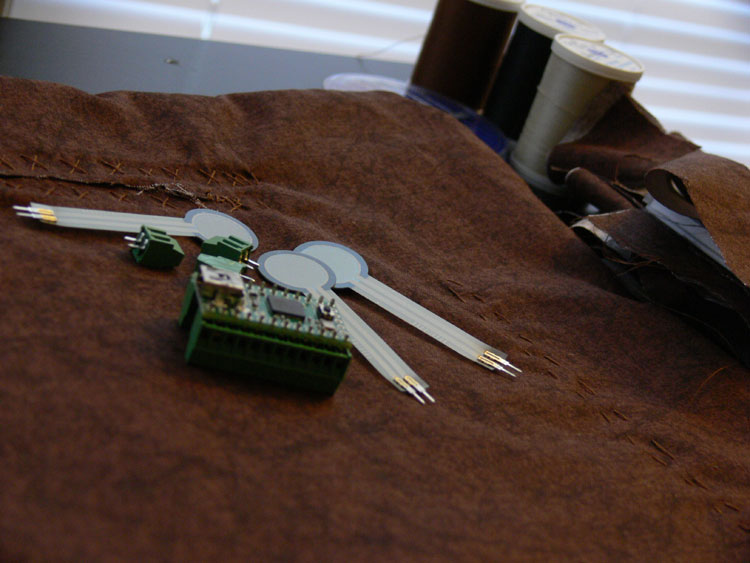
The hardware component of this project involves a pretty easy sensor/microcontroller/USB device combo. Its basically a pillow with force sensors shoved inside of it. I spent the last week sewing the pillow together as well as the zipper and internal pockets for holding the micro-controller board and sensors in place. When speaking to the people at Jo-Ann fabrics I learned that in order to get non-flammable stuffing it is hard to come by and quite expensive. I will be using dangerous cheap stuffing which is probably pretty flammable. For that reason I am going to attempt to place the micro-controller in an air-tight plastic enclosure. I have decided to go the quick route and use a teensy for the initial prototype as this is more of a software then hardware project unlike the RC Interceptor.In deciding what sensors to use, I came across a fun paper called "Squeeze Me: A Portable Biofeedback Device for Children" by Amy Parness, Ed Guttman, and Christine Brumback. They created a device from Dragon Skin Silicone that children can use to assist in rehabilitation from injury. I settled on pressure based resistors. Time will tell how well they work out.

Charles Palen has been involved in the technology sector for several years. His formal education focused on Enterprise Database Administration. He currently works as the principal software architect and manager at Transcending Digital where he can be hired for your next contract project. Charles is a full stack developer who has been on the front lines of small business and enterprise for over 10 years. Charles current expertise covers the areas of human pose estimation models, diffusion models, agentic workflows, .NET, Java, Python, Node.js, Javascript, HTML, and CSS. Charles created Technogumbo in 2008 as a way to share lessons learned while making original products.
Comments
No one has posted any comments yet, be the first
Comments are currently disabled.